Explanation Needed: How Encryption Keys Work
It's safe to say we're are officially well into the information age. Just about every device, from smartwatches to PCs and smartphones, store, transmit, and uses data. Sadly, all that information or data flowing via cable and WiFi are susceptible to being hacked. Luckily there's a technology that will make it very difficult for hackers to gain access to information. It's called encryption keys. How it functions is what we'll examine in-depth in this latest installment of Explanation Needed.
What exactly is encryption?
There are two separate stages encryption can be useful in transit, where you have data moved from end to end. Think the Internet, which continually has billions of data flowing endlessly. Then there is data that is at rest. Meaning dating stored on a storage drive.
Let us first turn our attention to in-transit encryption, as I mentioned in the above passage. Data is continuously flowing via the Internet. What this encryption does is ensure that the intended recipient can only read data sent—making it easy to understand the data using a sophisticated algorithm along with a key that converts it too hard to read data. The same algorithm and key is sent back to a recipient on the other end so it can easily be understood. The primary goal here is to thwart hackers from intercepting data in mid transmission, without the algorithm or key, the data will be unreadable.
There are two methods of encryption.
Image Source: 101 computing
There are two types of encryption methods, symmetric and asymmetric. With symmetric encryption, an encryption algorithm has been decided by both parties to encrypt the data. Using a mathematical algorithm called a cipher, which takes the readable data formed in plain text, then converts it to cipher-text, which is random data. For both parties to read the actual encrypted data, each needs to use a key, plug it directly into the chosen algorithm to encrypt the data. The very same key is then encrypted at the other end. Your wireless router uses this methodology. Most, if not all, wireless networks use the AES standard, which is an acronym for Advanced Encryption Standard. How this operates is all devices connected to your home WiFi network must support the same algorithm method along with your wireless router. When you create a password to your router, you're making a key that's plugged into your AES algorithm on your router, which scrambles data. It is then unscrambled by a device that's connected to the WiFi using that very same key. Remember, the primary purpose here is to make data unrecognizable to hackers.
Image Source: 101 computing
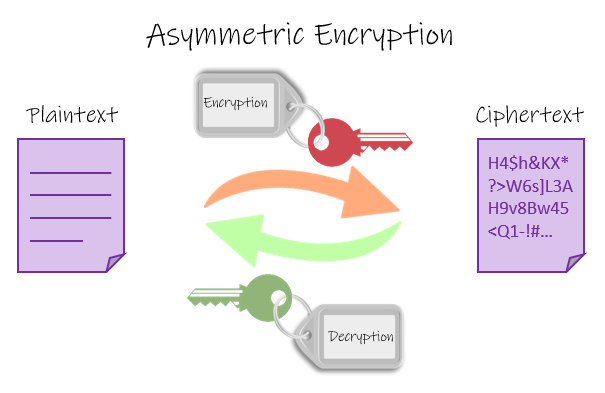
Now with asymmetric encryption, or better known as public-key encryption. How it functions is a bit more challenging to explain, but I'll do the best I can and simplify it all for you readers.
There is an agreed-upon encryption algorithm each party uses. But instead of one key, there are two that are linked. There's a private key which the party does not disclose, and there a public key anyone party can access. The private key encrypts the data sent to users, which then uses the public key to decrypt and read data. When the information is submitted back by the users, encrypted by their public key, only that private key can decrypt that particular data. Equate this to several individuals who have the same copies of keys to a house. Where in asymmetrical encryption, only one person has that key to the house. I did the best I can with that analogy, but I think you get the point.
Though asymmetrical encryption may seem very complicated and trust me, it is. It's a method used all the time when we browse the web. Many websites use asymmetrical encryption in the form of TLS or SSL. How would you know, you ask? Observe your URL; you'll see a lock icon in your browser along with HTTPS. When coming upon a website that uses SSL encryption, your computer will send a request to that particular site; the same website will provide a public key to your computer. It will then encrypt the data sent to the website. That website will use its private key to decrypt the data, which then encrypts it's own data and sends it back. When you make any purchases online, your credit card information is encrypted directly into the website using SSL encryption.
Adding a layer of encryption, the password manager
Password manager icons, you see it?
More people today are using third layer encryption that comes in the form of a password manager, which has become quite popular in the past few years. What's so unique about password managers is it allows users to download extensions into your web browser. It would then generate hard to guess passwords if you’re logging into certain websites. It then encrypts this information, which is only accessible by your master login. There is a slew of password managers of choice, LastPass, Kaspersky, NordPass, and 1Pasword, to name a few. My personal favorite is Dashlane. It has an intuitive interface across all platforms and allows any user to change almost all passwords instantly.
Encryption keys are a vital piece of technology and very much underrated. Imagine the Internet without it. You wouldn’t be able to do half things we’re so accustomed to doing now. Such as online shopping, view streaming content, I mean the list goes on. Pay your respect to the creators of encryption technology.